Understanding the NIST Framework
Regulation of cyber risk is growing for business owners across all market verticals served by Marlink; these companies will increasingly be called on to comply with industry standards, national regulation and regional regimes.
Enterprise users are subject to different cyber regulations depending on their location and sector of operations. Within the EU they are likely to be covered by NIS2. Financial institutions are subject to rules like DORA or PCI-DSS rules.
The biggest hurdles that enterprise users face in improving cyber security are not fully understanding the risks and not deploying enough resource to develop a systematic and comprehensive security program. Buying a product does not solve the challenge; security is multi-disciplinary challenge and it should be managed that way.
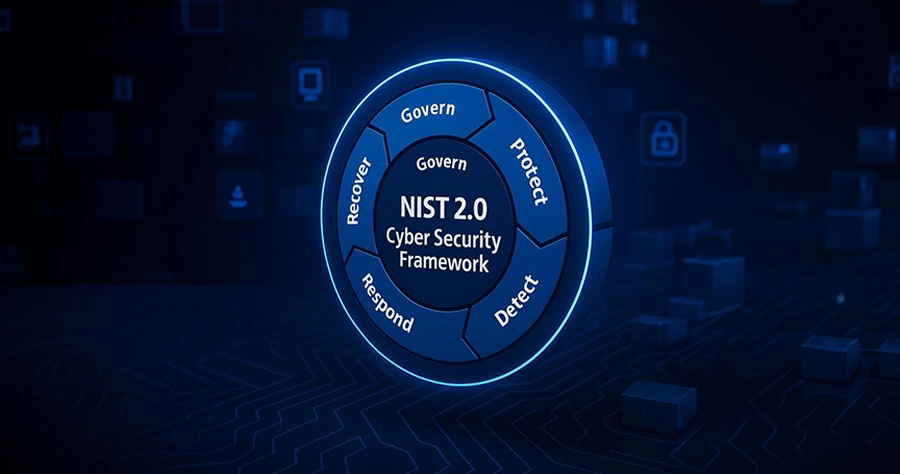
Where there is no direct regulation, best practise is for organisations to be compliant with standards like IEC or the NIST framework. By considering the six functions of the National Institute of Standards and Technology’s Cybersecurity (NIST) Framework, businesses can prepare for cyber incidents and take appropriate action to respond.
IDENTIFY - Develop an understanding of cyber security risks to facilitate their identification.
The main purpose of "Identify" is to make the assets on a network such as systems and network devices, "visible." Specifically, this involves creating an inventory of network assets covering the computer-based systems and equipment in use.
PROTECT - Establish safeguards to protect against cyber attacks.
The main purpose of "Protect" is to minimize the scale and frequency of potential cyber incidents. The requirements related to implementing necessary safeguards are specified. A particularly important aspect is "segmenting" the networks connected across a network. Segmentation means to partitioning computer systems based on their purpose and criticality in network design.
DETECT - Implement measures for detecting cyber incidents on board.
The main purpose of "Detect" is to find attacks. Specifically, it involves network operation monitoring and ensuring the effectiveness of onboard security functions. During normal operations, periodic functional verification is carried out, and in the event of anomalies, alarms are triggered to enable early recognition of cyber attacks or other threats that the asset owner has experienced.
RESPOND - Set up a protocol for responding to detected cyber attacks.
The main purpose of "Respond" is to examine and implement means to minimize the impact of detected cyber incidents. Specifically, it requires creating an Incident response plan that specifies how to respond to incidents and acting according to that plan.
RECOVER - Adopt procedures to recover any capabilities and/or services impaired by a cyber incident.
The main purpose of "Recover" is to an operational state after a disruption or failure caused by a cyber incident. By planning and implementing a recovery plan according to these requirements, CBSs and networks can be quickly restored. In the recovery plan, "roles and procedures for personnel in recovering from a cyber incident" and "management of backups, including maintenance and testing" are to be developed based on the company’s cyber policy.
GOVERN – Creating and upholding governance frameworks and processes to manage cybersecurity risks within an organisation efficiently.
This involves crafting and enforcing policies, procedures, and oversight mechanisms to ensure that cybersecurity initiatives align with business goals and comply with regulatory standards. Key activities include defining roles and responsibilities, implementing risk management frameworks, conducting regular cyber risk evaluations, and promoting a culture of cybersecurity awareness and responsibility throughout the organisation.
Get in touch
Contact us to find out how we can help you create new possibilities for your operations.
Insights
Read about our latest insights and explore the forefront of digital protection through our curated selection of news, articles, and expert blogs.